This Welsh password generator might keep you safe from hackers, but definitely from dragons | Boing Boing
Password faker generate a password that alice think it's a reference · Issue #176 · nelmio/alice · GitHub
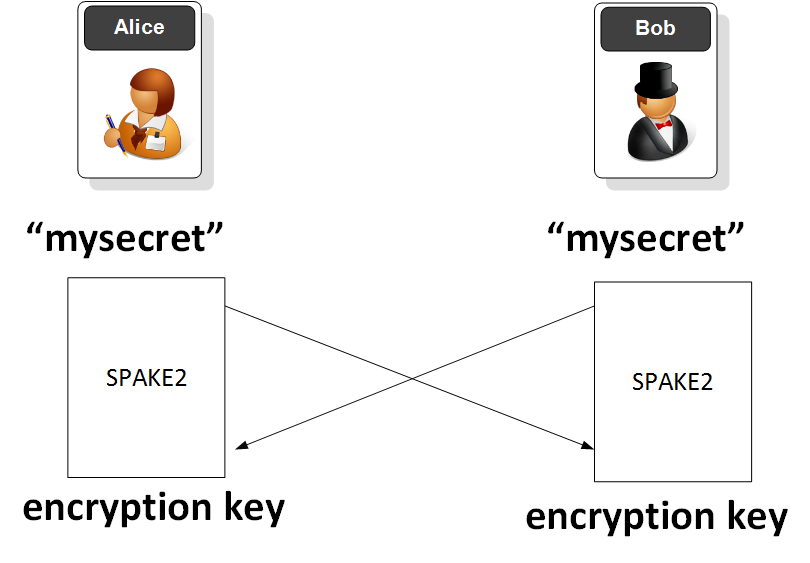
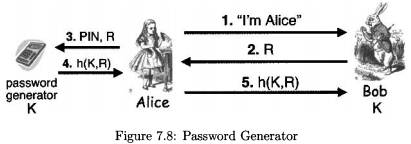
Why Do We Still Pass Passwords Over a Network — Meet PAKE? | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium
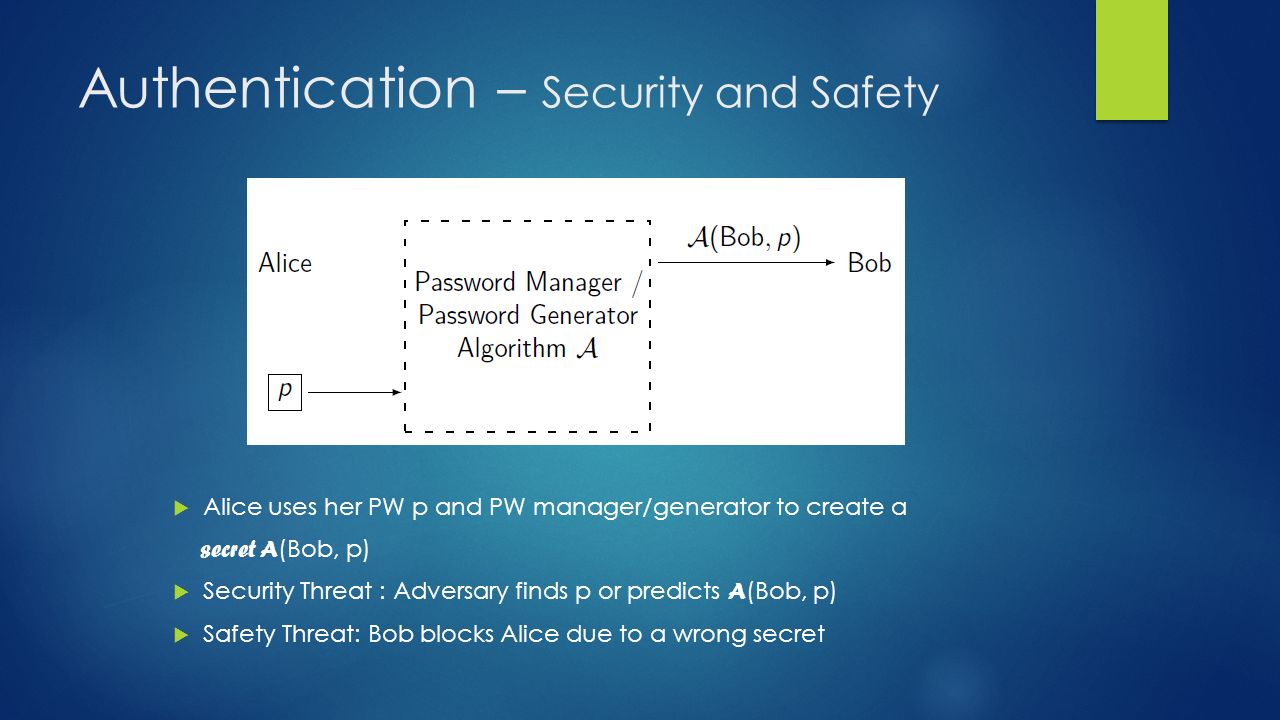
Knock Yourself Out Secure Authentication with Short Re-Usable Passwords by Benjamin Guldenring, Volker Roth and Lars Ries PRESENTED BY EUNYOUNG CHO COLLEGE. - ppt download


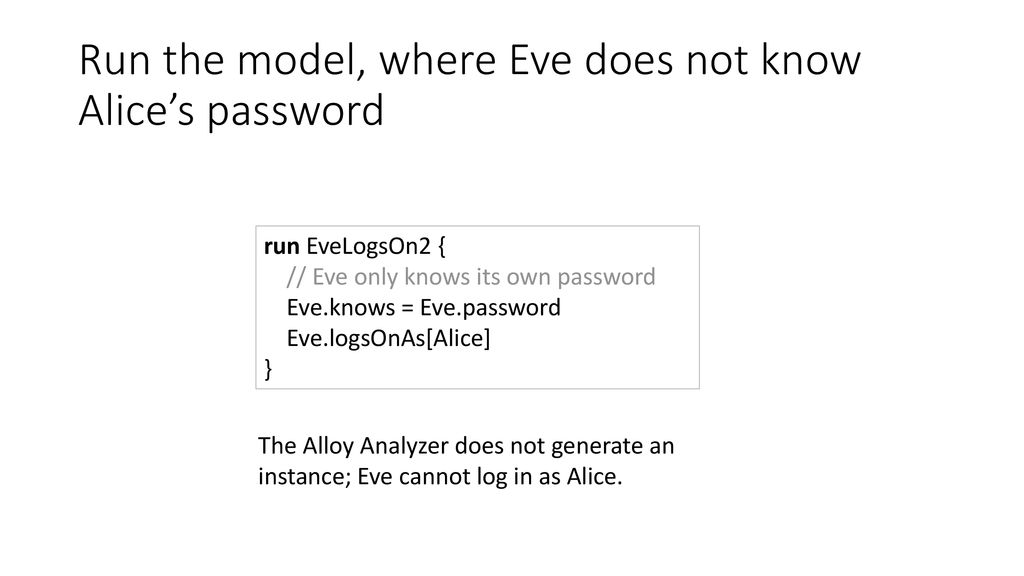
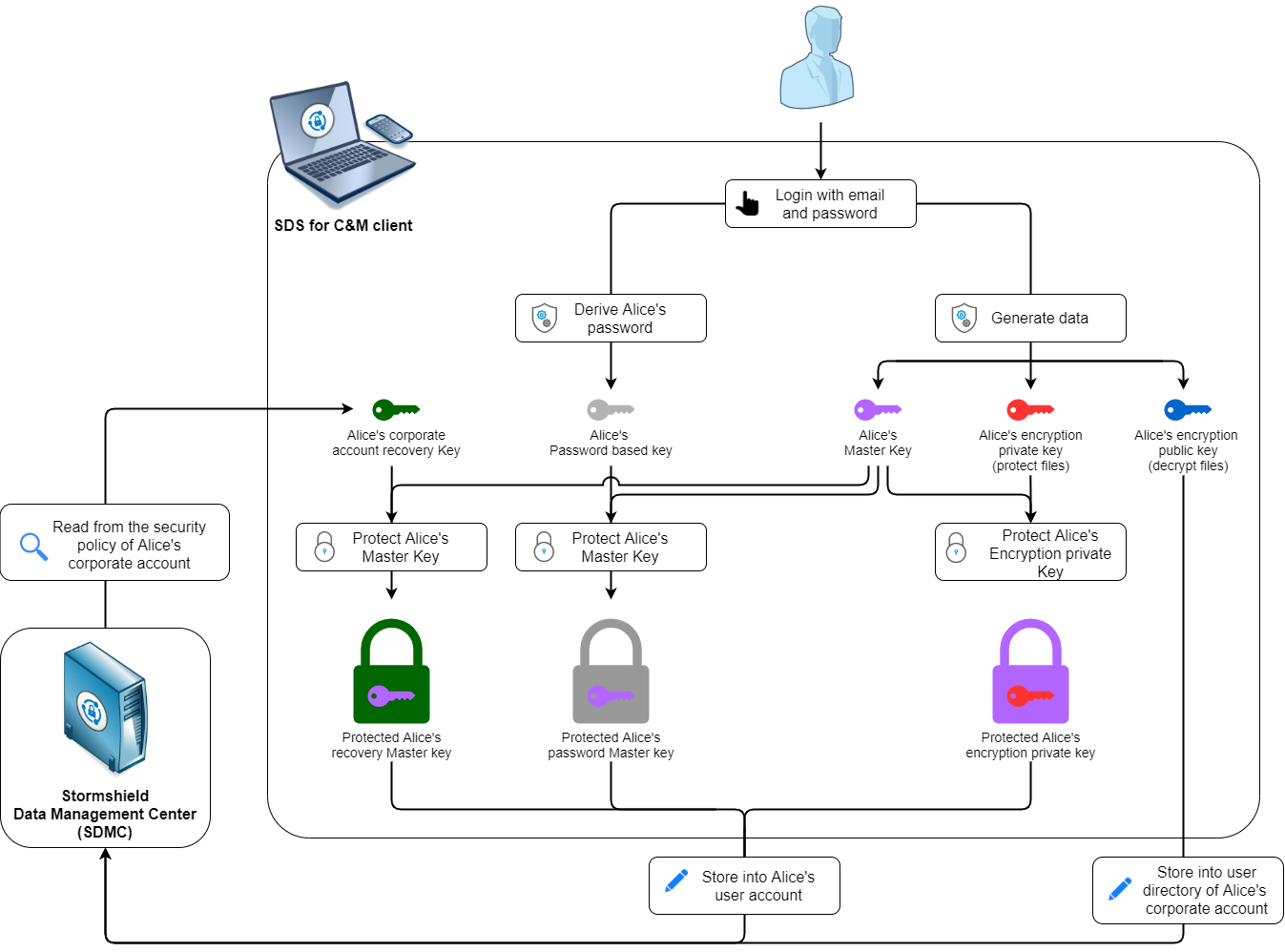
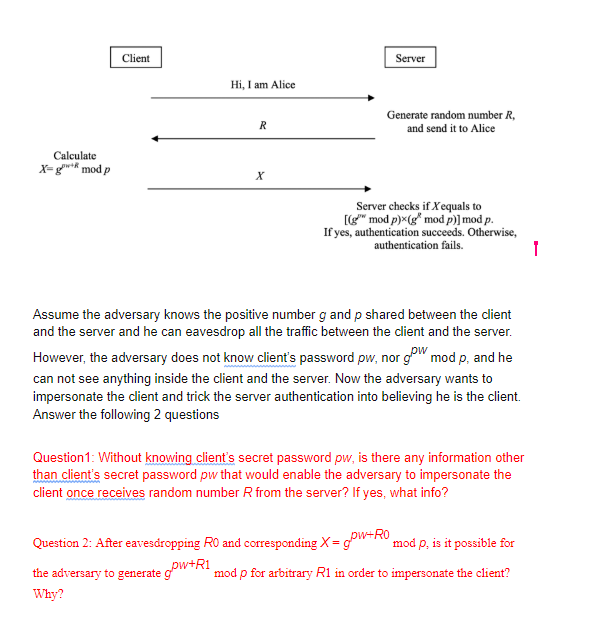


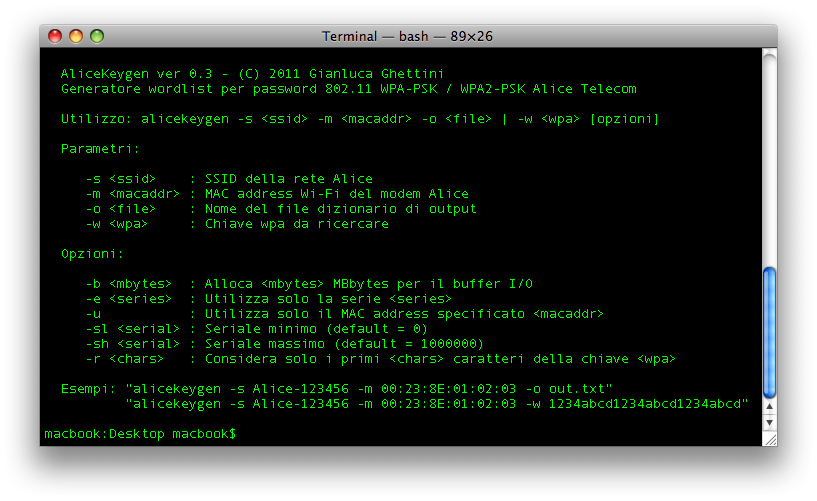


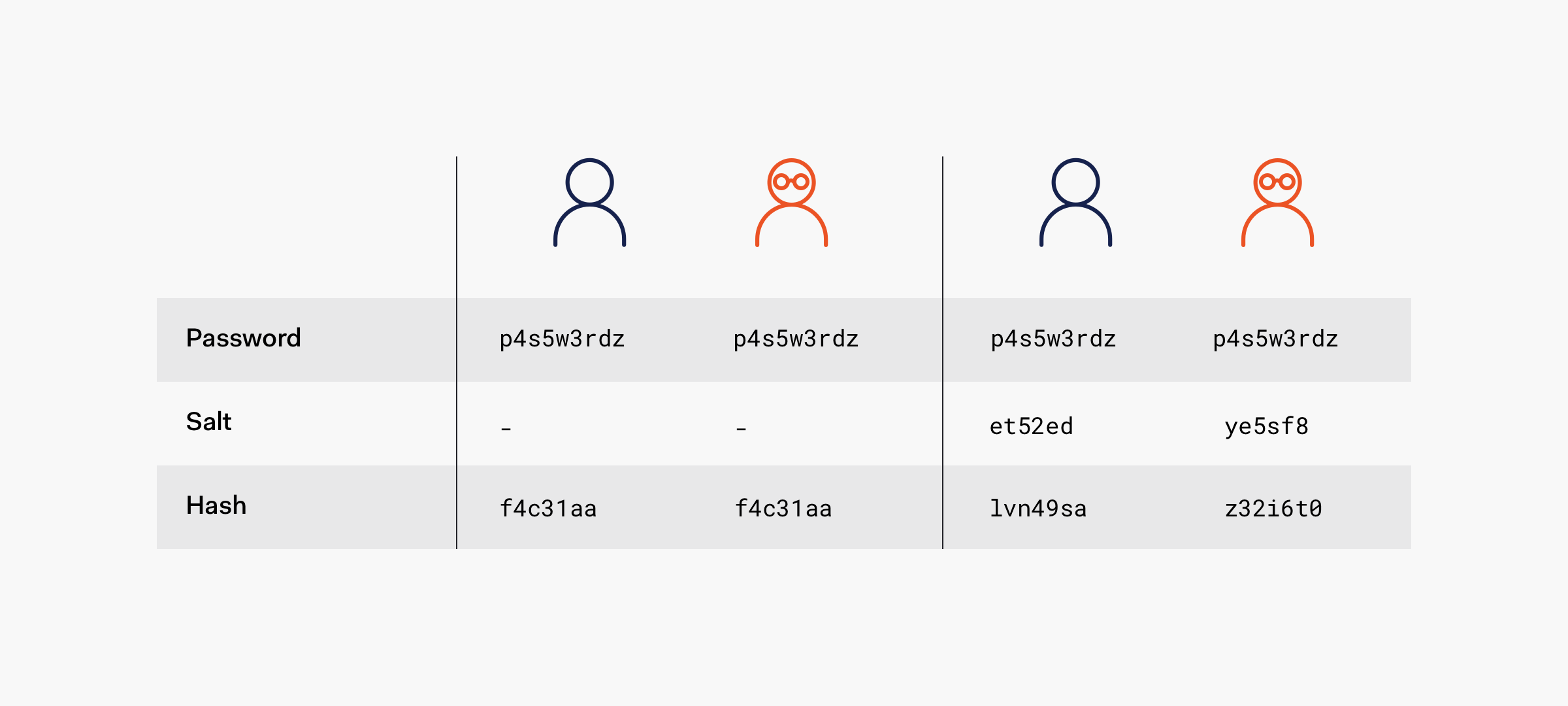
![PDF] Single password authentication | Semantic Scholar PDF] Single password authentication | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/0ad2cd1ebfd3aed4abe990ab1fce0a0381e3e2cf/16-Figure2-1.png)