Address behaviour vulnerabilities in the next generation of autonomous robots | Nature Machine Intelligence
GitHub - aliasrobotics/RVD: Robot Vulnerability Database. An archive of robot vulnerabilities and bugs.
![The ROBOT Attack: RSA Encryption Is Vulnerable – Choose ECC in TLS/SSL Certificates to Ensure Security [Article] - TRUSTZONE The ROBOT Attack: RSA Encryption Is Vulnerable – Choose ECC in TLS/SSL Certificates to Ensure Security [Article] - TRUSTZONE](https://trustzone.com/wp-content/uploads/2020/06/hero-illustration-knowledge-texts-01.png)
The ROBOT Attack: RSA Encryption Is Vulnerable – Choose ECC in TLS/SSL Certificates to Ensure Security [Article] - TRUSTZONE

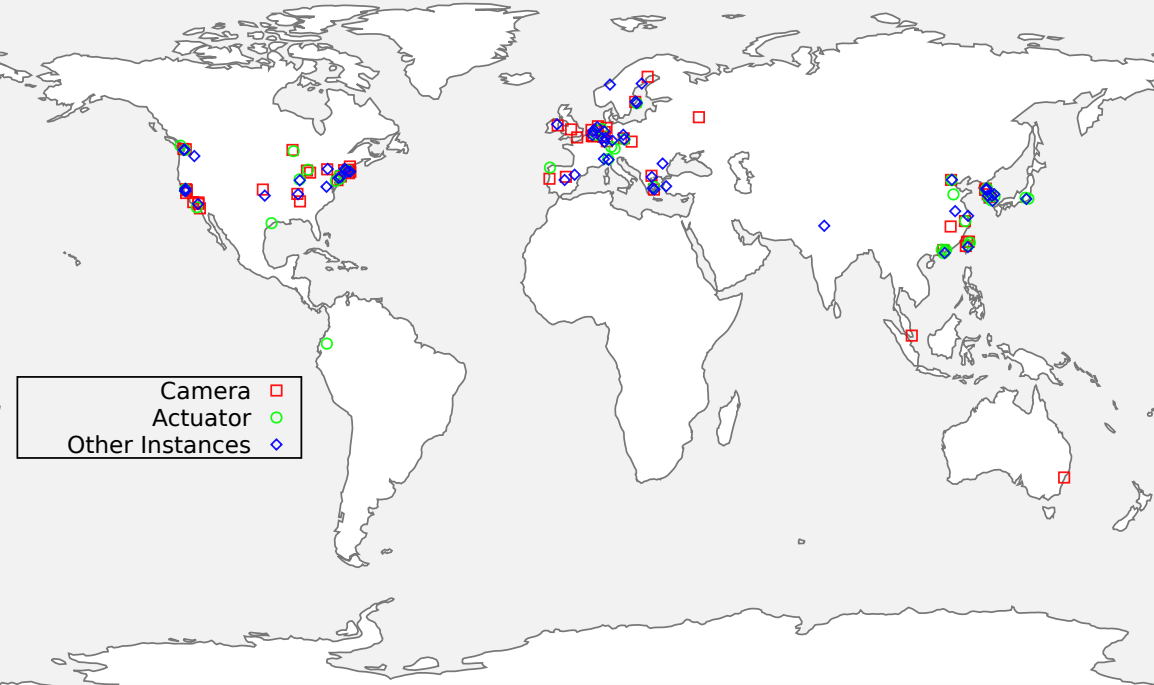
Components of Robot Vulnerability Scoring System version 1.0 (RVSS).... | Download Scientific Diagram
















.jpg)